A laptop is connected to a corporate LAN most days. Sometimes, the laptop's owner travels to a division of the company, and would like to use the laptop on the division's LAN. In addition, at night, the laptop's owner would like to connect the laptop to a LAN at home.
In the past, this situation would have required a fair bit of effort to accommodate. With clone interfaces, it's only necessary to create two clones of the original Ethernet interface, and give them the appropriate information. This is done by selecting the interface to clone and pressing the clone button. After giving the clone device a name (such as ``home''), you'll see a window similar to the one in Figure 4.
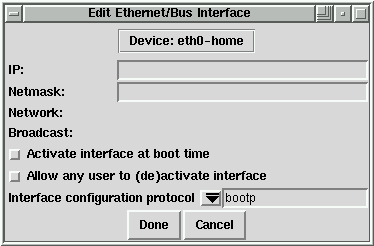
As you can see, you can specify an alternate IP address and netmask (the network and broadcast addresses are calculated automatically), or use bootp or dhcp to configure the interface. In addition, the clone device may be configured to start automatically at boot time, and can be set so that any user may bring the interface up or down.
1.3.6 New Diskette Group
Red Hat Linux 5.0 also includes a new group that system administrators can use to give certain users access to the system's diskette drive. This can be done explicitly, or via the pam_env module.
1.3.7 Anti-spam changes to sendmail
Sendmail version 8.8.7 is included with Red Hat Linux 5.0. Also included are rulesets that discourage the distribution of unsolicited commercial e-mail (also known as ``spam''). These rulesets were created by Claus A\betamann. Although some information is included below, please consult Claus' web page documenting his changes at:
http://www.informatik.uni-kiel.de/%7Eca/email/check.html
Please Note: In this release of Red Hat Linux, sendmail does not relay by default. Because of this, if your Red Hat Linux system must act as a relay, please review the following information.
1.3.7.1 Overview
This release has been configured to take advantage of the latest changes to sendmail to prevent spam by the addition of new sendmail rulesets.
The following rulesets have been added to the S98 (local additions) section of /etc/sendmail.cf:
- junk
- check_mail
- check_rcpt
- remove_local
- junkIP
- check_relay
The actions of these rulesets are controlled by the following files in the /etc/mail directory:
- ip_allow
- name_allow
- relay_allow
- deny
Let's take a look at each of these files.
1.3.7.2 ip_allow
This is a flat text file that contains the addresses or networks of hosts that are allowed to use this this host as a relay.
The format for this file is:
These lines represents a host address, a class C network, a class B network and a class A network, respectively.hhh.hhh.hhh.hhh ccc.ccc.ccc bbb.bbb aaa
1.3.7.3 name_allow
This is a flat text file that contains the hostnames or domain names of hosts that are allowed to use this host as a relay.
The format for this file is:
hostname.domain.com domain.com
These lines represent a hostname and a domain name.
Please Note: Hosts not 'included' in either ip_allow or name_allow will be given an error message of "551: xxx, we do not relay" where xxx is the RCPT address that was given.
1.3.7.4 relay_allow
This is a flat text file that contains the hostnames, domain names, host addresses or networks for which this machine will relay to:
The format for this file is:
hostname.domain.com domain.com hhh.hhh.hhh.hhh ccc.ccc.ccc bbb.bbb aaa
The formats in this file are the same as for the ip_allow and name_allow files described earlier.
Please Note: Since ip_allow, name_allow and relay_allow are plain text files, any changes to them will necessitate restarting sendmail. This can be accomplished by executing the followin commands:
/etc/rc.d/init.d/sendmail stop; /etc/rc.d/init.d/sendmail start.
1.3.7.5 deny
This is a flat text file that must be converted into a hash database file
with
makemap(8) before use. This file contains a set of email addresses,
hostnames, domain names, host addresses, or network addresses seperated by
a tab from an error message.
The format for this file is:
user@domain.com<tab>error message 0 hostname.domain.com<tab>error message 1 domain.com<tab>error message 2 hhh.hhh.hhh.hhh<tab>error message 1 ccc.ccc.ccc<tab>error message 3 bbb.bbb<tab>error message 4 aaa<tab>error message 5
Each line represents the identification of a known spammer. When an email address is specified in this file, the error message provided will be returned to the spammer's MTA. For the other formats, the corresponding error message will be logged to /var/log/maillog, and "550 Access denied" is returned to the spammer's MTA.
The following command can be used to create the hash database version of this file:
makemap -v /etc/mail/deny < /etc/mail/deny
The output from this command is the database file /etc/mail/deny.db.